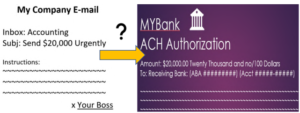
Recently, a few of our clients have experienced unrecoverable losses due to fraud activity:
- One client received an e-mail from a spoofed vendor e-mail account requesting future payments be made to a new bank account. The new bank, of course, belonged to a bad actor. Loss $20,000.
- Another client received what appeared to be an authentic email from their CEO urgently requesting funds, traditionally made by check, be wired to a bank account. The Accounting Manager complied, and the company lost $18,000.
- Yet another client was contacted by a “spoofed” vendor, whose accounting system had been hacked, and requested an urgent payment to allow them to stay in business. Our client complied, but the funds had been redirected to the hackster’s bank account. Loss $10,000.
The losses had several things in common and should serve as red flags:
- The request for funds appeared authentic and to come from a known source.
- The request came with some urgency, requesting immediate attention.
- Our client’s trusted employee was authorized to initiate ACHs/wires by themselves, without a second bank-authenticated approval source.
- The request came with some change in existing protocol, and
- The amount, while significant, was not so large as to cause undue attention, and/or was in keeping with the vendor’s normal dollar volume for the transaction in question. This could be a sign that someone’s email was compromised, or the threat actor was gathering the intel somewhere else.
This is a warning to the unwary
Business Email Compromise is becoming prevalent, and the fraudulent perpetrators are resourceful. While all fraud is not preventable, there are a number of steps you can take to reduce your risk of this type of activity.
- First, and foremost, train your employees who handle cash to adopt a Zero Trust mentality. A recent article by Deloitte published in the Wall Street Journal entitled, “a CFO Guide to ‘Zero Trust’ Cybersecurity”[i] contains some excellent tips. “Familiar, ‘trust but verify’ is being supplanted by ‘never trust, always verify’” approachibid. Consider this a journey and not a goal, if you are a small or medium-sized enterprise.
- Require two-factor authentication by independent company officials on all outgoing electronic fund transfers (above very de minimis levels). The second authenticator should not be a rubber stamp to the first.
- Be skeptical of any change in protocol. When in doubt, do not respond to the sender by the same communication means received, but initiate a separate outgoing communication to a known “good” address or phone number, other than the one received, confirming the request, before paying. Often a spoofed e-mail address can be identified by holding (but not clicking!) the cursor over the stated e-mail address to identify the true link-to website. Never click on hyperlinks from unknown senders. Be wary of poor grammar or misspellings.
- Be particularly skeptical of any request requiring immediate action. Slow down. Take your time!
- Use encrypted e-mails, such as provided through certain Microsoft and Google plans or a 3rd party service such as AppRiver/Zix or Bracket through a Virtual Private Network (VPN). A VPN does not necessarily encrypt email contents, just the traffic connection that transports the email.
- Configure e-mail systems to allow in only known senders. (See DKIM, DMARC, and SPF: Setting Up Email Security (howtogeek.com)
- Have your e-mail system flag phishing e-mails or send them to spam by optimizing native spam filtering settings through your Mail provider or through a 3rd party tool such as MailProtector or Mimecast. More and more, we’re seeing e-mails flagged with, “*** External email: Please be careful when opening attachments or clicking links. ***” warnings.
- Use encrypted passwords, such as employed by Password Managers. Change your passwords frequently. Again, Password Managers facilitate this process.
- Inform your customers, that changes to bank accounts or lock boxes will only be made through secure file transfers or secure file sites, such as SafeSend or ShareFile. Do not accept any change in protocols from any other source.
- Modify customer contracts to establish secure protocols for payments and how changes in protocols are to be securely affected.
- Obtain Cyper insurance. CyberInsurance is available, including Business E-Mail Compromise, which is generally a feature of a more comprehensive package. That having been said, there is no standard blanket policy, and carriers tailor individual policies to specific policy holders. Best to work with both your IT provider and an experienced insurance broker to assess the coverage required. Premiums vary widely and are heavily impacted by claims experience.
At the 2Go Advisory Group, we’re offering a fee-based Treasury Assessment and employee training to review your Treasury protocols and provide recommendations for strengthening your controls. Contact Chris Chillingworth, Partner, at cchillingworth@cfos2go.com if interested.
Contributors:
Alex Rayter, Phoenix 2.0
Brian Barnier, Value Bridge Advisors
 Chris Chillingworth is a Partner with CFOs2Go, a division of the 2GoAdvisory Group, and leads our High Tech and Manufacturing, Financial Systems and Technical Accounting Practice Groups. He has over 35-years’ experience as a C.F.O. for both public and private companies, a real estate development entrepreneur, and financial consultant to many small and medium enterprises (SMEs). Chris began his career at Ernst & Ernst (now Ernst & Young) and is a licensed CPA (Inactive). He periodically lectures and blogs on topics of financial interest
Chris Chillingworth is a Partner with CFOs2Go, a division of the 2GoAdvisory Group, and leads our High Tech and Manufacturing, Financial Systems and Technical Accounting Practice Groups. He has over 35-years’ experience as a C.F.O. for both public and private companies, a real estate development entrepreneur, and financial consultant to many small and medium enterprises (SMEs). Chris began his career at Ernst & Ernst (now Ernst & Young) and is a licensed CPA (Inactive). He periodically lectures and blogs on topics of financial interest
—————————–
[i] Originally published in the Wall Street Journal, Aug 27, 2021 4:00 PM ET.
